Part of a series of posts related to the cloud security company Duo Security, Inc. I am not affiliated in any way with Duo Security (please read my more extensive disclaimer below), I’m just doing my best to understand their offering.
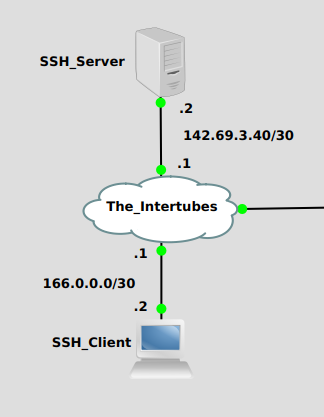
Following the very clear instructions I found on https://duo.com/docs/duounix, I proceed to Duo my SSH. This is my topology:
I start by getting my Ubuntu 18.04 Server ready. Duo says we’ll be building from source and I need a compiler like GCC so I just installed the build-essential package. I also need libssl-dev and libpam-dev.
sudo apt-get install build-essential libssl-dev libpam-devThen I need to get the pam_duo source, untar and compile.
wget https://dl.duosecurity.com/duo_unix-latest.tar.gz
tar zxf duo_unix-latest.tar.gz
cd duo_unix-1.11.2
./configure --with-pam --prefix=/usr && make && sudo make installThe make program then spits out a bunch of gibberish that I will never understand, but I know it compiled ok because it didn’t say “error” a bunch of times. I’m very precise like that.
Next up I copy the keys and API hostname (the magic link to my Duo account) found when I click “Protect this application” on my Duo account under “applications”:
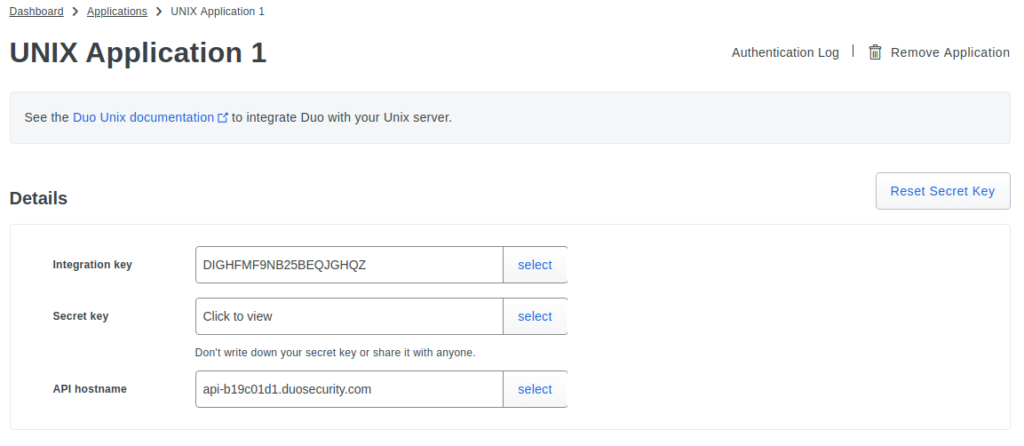
Then I put them in /etc/duo/pam_duo.conf file. It should look like this, according to the Duo documentation:
[duo]
; Duo integration key
ikey = DIGHFMF9NB25BEQJGHQZ
; Duo secret key
skey = NOTGONNATELLU
; Duo API hostname
host = api-b19c01d1.duosecurity.comThen edit the pam sshd configuration file /etc/pam.d/sshd, find this line and comment it:
@include common-authThen add three lines so it looks like this:
auth [success=1 default=ignore] /lib64/security/pam_duo.so
auth requisite pam_deny.so
auth required pam_permit.soLastly, restart the sshd daemon to apply the changes to sshd and duo.
sudo systemctl restart sshdOnce I get that all in place, I try SSHing (is that a word?) from the client to the server:
james@client:~$ ssh james@142.69.3.42
Please enroll at https://api-b19c01d1.duosecurity.com/portal?code=ca487343d044ab35&akey=DAVEM6A3YS7ML96IE4BJ
james@142.69.3.42's password:I need to enroll my MFA device (my android phone) at https://api-b19c01d1.duosecurity.com/portal?code=ca487343d044ab35&akey=DAVEM6A3YS7ML96IE4BJ, so I head on over there and follow the prompts:


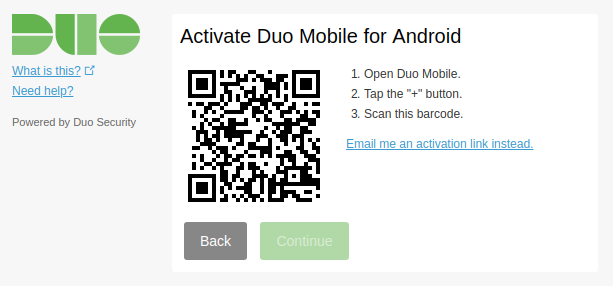

Then I try again SSHing from the client to the server. This time I get an MFA prompt on the command line:
james@client:~$ ssh james@142.69.3.42
Duo two-factor login for james
Enter a passcode or select one of the following options:
1. Duo Push to XXX-XXX-7273
2. Phone call to XXX-XXX-7273
3. SMS passcodes to XXX-XXX-7273
Passcode or option (1-3): 1Entering option 1 gets me a prompt from my Duo Push app on my phone to accept or deny the request (the app restricts taking a screenshot so I couldn’t include it, sorry), options 2 and 3 are pretty much what they look like.
Success. Logging you in...
Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 4.15.0-20-generic x86_64)
Last login: Mon Jun 24 20:35:10 2019
james@server:~$There is much rejoicing.
Non-Affiliation Disclaimer:
I am not affiliated, associated, authorized, endorsed by, or in any way officially connected with Duo Security, or any of its subsidiaries or its affiliates. The official Duo Security website can be found at https://duo.com. The name Duo Security as well as related names, marks, emblems and images are registered trademarks of its owners.


damn nice work. Been looking for something like this lab for gns3 for a while. Thanks!!
Thanks!