Running a syslog server that can collect logs from various devices on your network is really simple with Ubuntu Server 20.04. Using built-in software Rsyslog, you can quickly configure it to be either a syslog client or a server. Since most network devices have the capability to send logs to an external server, you can quickly set up your Ubuntu server act as a central log collection point.
What many folks don’t know is that syslog is actually a standard application-layer network protocol, not just software. It is defined in RFC 5424. It’s because of this standard protocol that network devices and servers alike are able to easily send and store logs. Without a standard protocol, it would be much more difficult to pull that off.
Let’s set up syslog on Ubuntu 20.04!
Topology
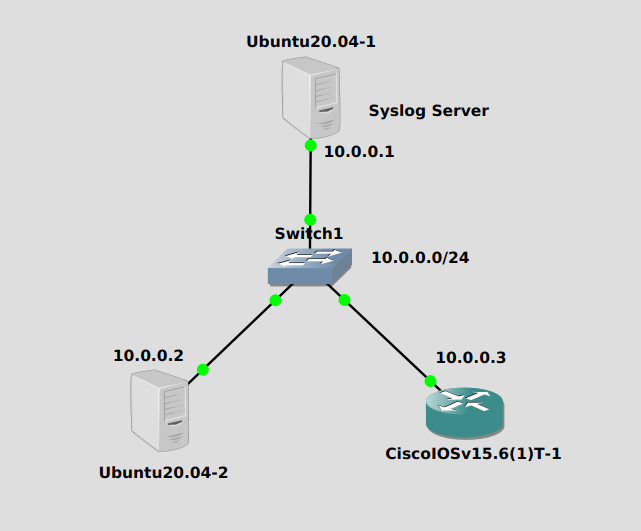
The Ubuntu server at 10.0.0.1 will act as our syslog server while the other Ubuntu server and Cisco router will act as clients, sending their logs to the server.
Server Configuration
Since Rsyslog is already installed on Ubuntu (and others), there’s no installation. First we need to edit /etc/rsyslog.conf and uncomment these lines:
module(load="imudp") input(type="imudp" port="514") module(load="imtcp") input(type="imtcp" port="514")
They will activate the server on TCP and UDP port 514 for incoming syslog messages. With just this configuration, the syslog server will work. But we’ll make one more modification – we want each IP address to have it’s own file. Otherwise all messages get dumped in the main file at /var/log/syslog.
We’ll create a file at /etc/rsyslog.d/30-custom.conf and place a couple of simple rules in it:
if $fromhost-ip startswith '10.0.0.2' then /var/log/network/10.0.0.2.log & stop if $fromhost-ip startswith '10.0.0.3' then /var/log/network/10.0.0.3.log & stop
Create and change the ownership of the /var/log/network directory:
mkdir /var/log/network chown syslog:adm /var/log/network
And restart Rsyslog:
systemctl restart rsyslog
And we’re done!
Client Configuration
For a Cisco IOSv device, the following command will turn on logging to a remote server:
logging host 10.0.0.1
For Ubuntu, just add the following line to /etc/rsyslog.conf:
*.* @@10.0.0.1:514
And restart the service:
systemctl restart rsyslog
Verification
To verify that syslog messages are in fact going to the server, we need to initiate an event.
For Cisco IOSv, shutting/no shutting any interface will do the trick. In config mode on the interface, just issue these commands:
Router(config-if)# shut Router(config-if)# no shut
While you might be tempted to go check /var/log/network/10.0.0.2.log right away for syslog messages, it might be worth it to do a packet capture first to see if logs are indeed leaving the Cisco router and heading for the syslog server.
A capture between the two shows the following lone packet when we issue those shut commands:
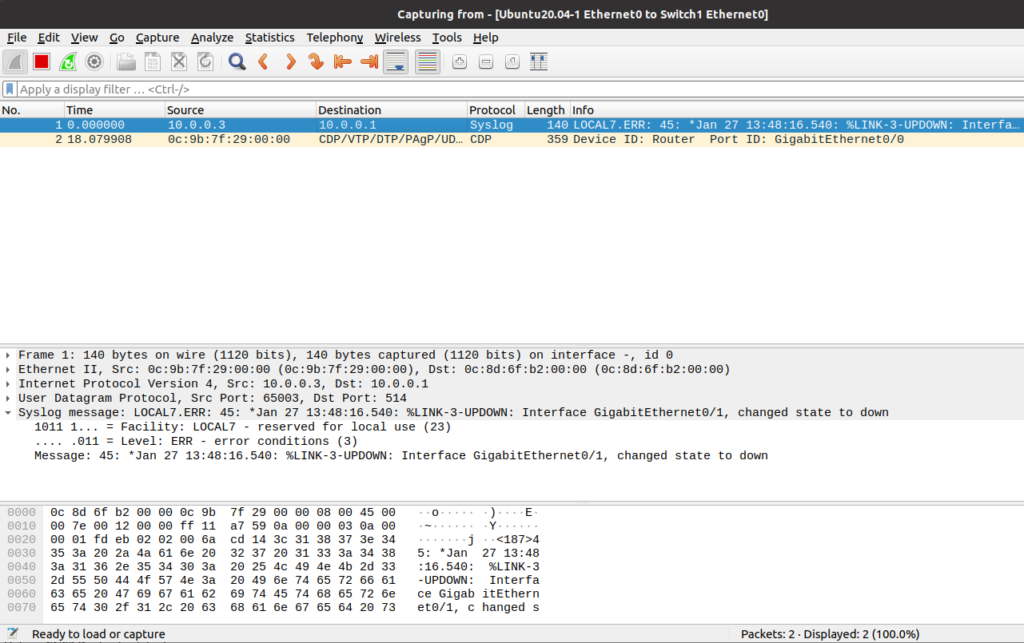
Then check the /var/log/network/10.0.0.3.log on the syslog server to see if the message was properly written:
cat /var/log/network/10.0.0.3.log --- Jan 27 13:48:17 10.0.0.3 45: *Jan 27 13:48:16.540: %LINK-3-UPDOWN: Interface GigabitEthernet0/1, changed state to down
Initiating an event on the Ubuntu client is as easy as shutting down a service (I’m sure there’s others too). I happen to have Nginx web server running on this guy so I’ll stop it:
systemctl stop nginx
The in the file on the syslog server:
cat /var/log/network/10.0.0.2.log --- Jan 27 23:21:21 u20vm systemd[1]: Stopping A high performance web server and a reverse proxy server... Jan 27 23:21:21 u20vm systemd[1]: nginx.service: Succeeded. Jan 27 23:21:21 u20vm systemd[1]: Stopped A high performance web server and a reverse proxy server.
Hope you liked this one.
