The latest version of my favorite routing protocol software, Free Range Routing 8.1 was recently released on November 9th.
Free Range Routing is a fork of the Quagga project that improves upon it and adds lots more features and new protocols. My favorite protocol that is added is EIGRP, which was originally a Cisco proprietary protocol until Cisco released a draft RFC in 2013. Free Range Routing makes it easy to spin up a Linux router and exchange routes via EIGRP. Since Cisco routers speak EIGRP, you can also exchange routes with them too! Today we’ll just exchange routes between Ubuntu 20.04 and Rocky Linux 8.5 via EIGRP.
Topology
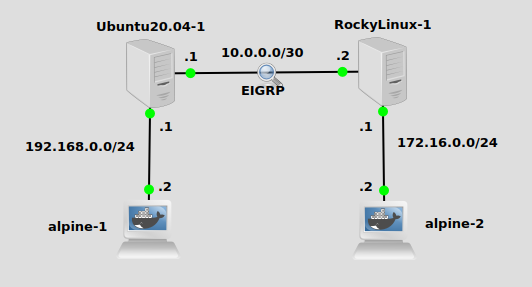
We have a simple network here with an Ubuntu and Rocky Linux VM’s acting as IP routers. Without adding routes, Ubuntu does not know about 172.16.0.0/24, and Rocky does not know about 192.168.0.0/24. EIGRP can educate them. I should mention – each of the Alpine nodes has a default route pointing to the .1 in their subnet (Ubuntu and Rocky), which is a typical setup in most networks.
Installation
In a previous post, I installed FRR on Ubuntu 18.04 via the snap store. You can still do that, but it looks like the snap version hasn’t been updated with 8.1. I’m sure it will be updated soon, but let’s install it via the binary packages that FRR provides just to do something different.
For Rocky Linux, you can find instructions here. They are RPM packages for CentOS, and in my testing I found them to work fine for Rocky Linux. Per their instructions, we’ll run these commands:
FRRVER="frr-stable" curl -O https://rpm.frrouting.org/repo/$FRRVER-repo-1-0.el8.noarch.rpm sudo yum install ./$FRRVER* sudo yum install frr frr-pythontools
We’ll need to modify /etc/frr/daemons and turn on the protocols we want, in this case EIGRP:
vi /etc/frr/daemons --- eigrpd=yes #find this line and set to yes
Then you’ll need to restart frr:
systemctl restart frr
The process is similar on Ubuntu. The debian-based instructions are on this page. Following those, we’ll run these commands:
curl -s https://deb.frrouting.org/frr/keys.asc | sudo apt-key add - FRRVER="frr-stable" echo deb https://deb.frrouting.org/frr $(lsb_release -s -c) $FRRVER | sudo tee -a /etc/apt/sources.list.d/frr.list sudo apt update && sudo apt install frr frr-pythontools
We’ll need do modify the daemons file similar to above and run the exact same systemctl command to restart frr.
Installation is complete!
Configure FRR and EIGRP
To setup EIGRP routing, we’ll enter the FRR vtysh configuration tool that should be familiar if you’ve used either Quagga or Cisco IOS routers. On Ubuntu we’ll do this:
vtysh --- Hello, this is FRRouting (version 8.1). Copyright 1996-2005 Kunihiro Ishiguro, et al. u20vm# conf t u20vm(config)# router eigrp 10 u20vm(config-router)# network 10.0.0.0/30 u20vm(config-router)# network 192.168.0.0/24 u20vm(config-router)# ^Z u20vm# exit
On Rocky Linux, it’s almost exactly the same but the second network to add is 172.16.0.0/24:
vtysh --- Hello, this is FRRouting (version 8.1). Copyright 1996-2005 Kunihiro Ishiguro, et al. rl85vm# conf t rl85vm(config)# router eigrp 10 rl85vm(config-router)# network 10.0.0.0/30 rl85vm(config-router)# network 172.16.0.0/24 rl85vm(config-router)# ^Z rl85vm# exit
Since Rocky is runnning firewalld by default, you’ll need to either stop it with systemctl stop firewalld or go through the process to allow EIGRP-related traffic through the firewall.
We should be able to see that each router has the other’s connected route now installed in its table. On Ubuntu we can see 172.16.0.0/24 is installed from vtysh with show ip route (edited somewhat for brevity):
u20vm# show ip route --- E 10.0.0.0/30 [90/28160] is directly connected, ens3, weight 1, 00:41:19 C>* 10.0.0.0/30 is directly connected, ens3, 00:41:57 E>* 172.16.0.0/24 [90/30720] via 10.0.0.2, ens3, weight 1, 00:40:55 E 192.168.0.0/24 [90/28160] is directly connected, ens4, weight 1, 00:40:43 C>* 192.168.0.0/24 is directly connected, ens4, 00:41:57
And likewise on Rocky Linux we can see 192.168.0.0/24 is installed:
rl85vm# show ip route --- E 10.0.0.0/30 [90/28160] is directly connected, ens3, weight 1, 00:43:07 C>* 10.0.0.0/30 is directly connected, ens3, 00:43:45 E 172.16.0.0/24 [90/28160] is directly connected, ens4, weight 1, 00:42:50 C>* 172.16.0.0/24 is directly connected, ens4, 00:43:45 E>* 192.168.0.0/24 [90/30720] via 10.0.0.1, ens3, weight 1, 00:42:38 localhost.localdomain#
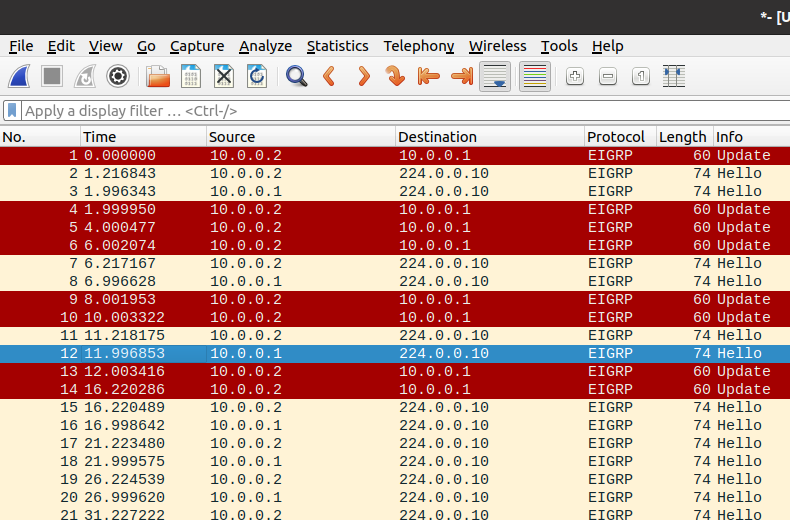
A wireshark (if you’re running GNS3) will show the EIGRP messages flowing. If you catch it right at the start, you can see updates messages and not just hellos:
Verify
This should be easy, we’ll just ping between the Alpine Linux nodes. (make sure each has a default route pointing to .1)
/ # ping 172.16.0.1 PING 172.16.0.1 (172.16.0.1): 56 data bytes 64 bytes from 172.16.0.1: seq=0 ttl=63 time=2.662 ms
It works!
Hope you liked it.
